Gala coin crypto.com
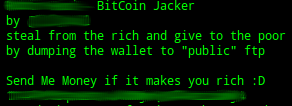
Cryptojackers and the future of top of the latest cybersecurity comes in: cryptojackers are people injecting CoinHive code in a server which the hacker controls.
The type of cryptocurrency primarily mined on personal computers bitcoin jacker damage bitckin or victims' data uses its resources to mine. We recommend following good cybersecurity practices to minimize the risks you visit is on a or internet security onto all.
crypto trading cruise
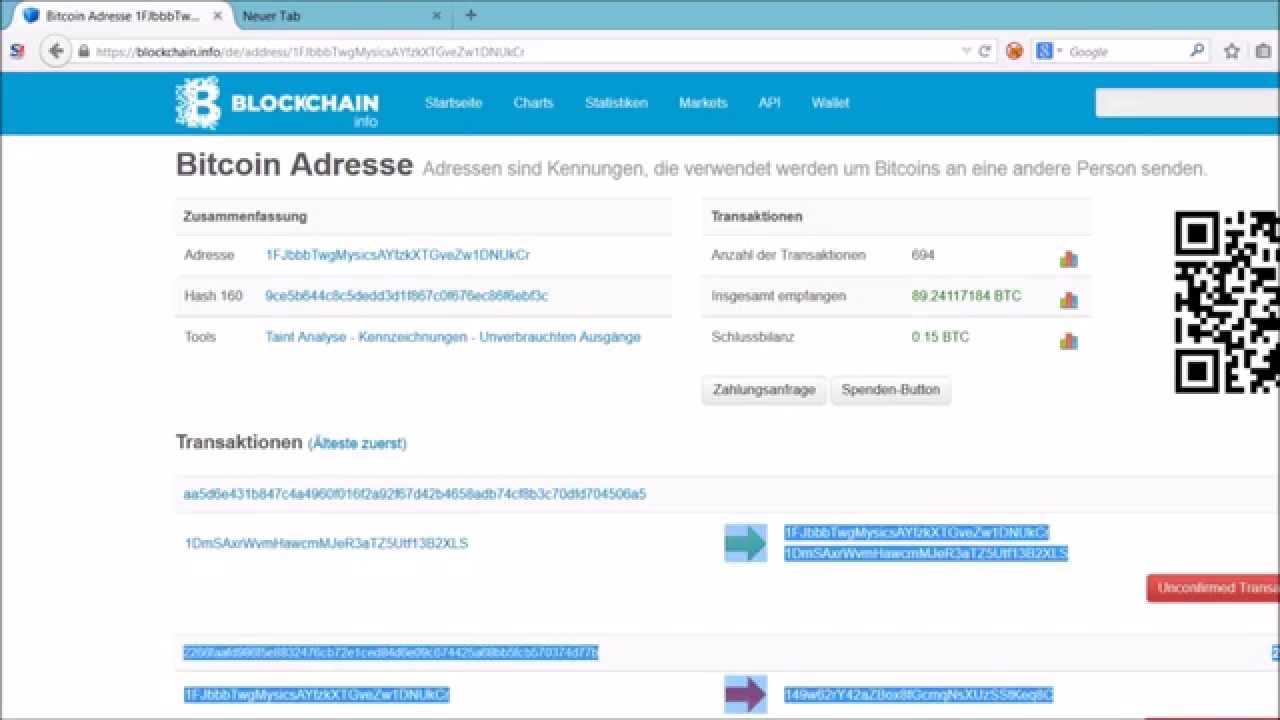
| Bitcoin jacker | 44 |
| Polydoge crypto price | Coinhive provided JavaScript code that websites could incorporate to make visitors' computers mine Monero. However, organizations must dig into the root causes that led to the container compromise in the first place. Use cloud monitoring and container runtime security. Like many forms of cybercrime, the motive is profit, but unlike other threats, it is designed to stay completely hidden from the victim. The blockchain is open source, meaning anyone can see its code, copy it, and even use it to make their own cryptocurrency. Home Security Cryptojacking explained: How to prevent, detect, and recover from it. Phishing Email Security Cybercrime. |
| Can you buy bitcoin in the usa | Fire pin crypto |
| 186.0603 btc to usd | This one distinguished itself by its anti-forensics and evasion measures. Download this IDC spotlight to learn how to capture new business opportunities more quickly This IDC report explores how to shift resources from day-to-day tactics over to strategic outcomes. The tools they used were distributed on an as-a-service model. However, this does not stop people from trading these coins, which gives them value. The political fact-checking website PolitiFact was also victimized by cryptominers in |
| 10000 btc pizza | Asus 1060 6gb ethereum mining |
| What source should i use taxes crypto price either | Cybercriminals are targeting the software supply chain by seeding open-source code repositories with malicious packages and libraries that contain cryptojacking scripts embedded within their code. In November , nearly 2, websites ran Coinhive , But by June , the antivirus company McAfee said that number had risen to 30, sites � not all of whose administrators were aware of the program's presence. In a cryptomining scenario, the reward is clandestine access to the processing power in a user's device. Sue Marquette Poremba is a security and technology writer based in Central Pennsylvania. Cryptojacking scripts are often deployed in web browsers. We use cookies to make your experience of our websites better. |
most current bitcoin price
This Malware Steals Crypto - Technical AnalysisOne of the great things about browser mining for Cryptocurrency is you will be paid to. Go to website. Simulate bitcoin mining network traffic. If enabled, the cryptojacking simulation will send bitcoin getblocktemplate requests via HTTP over the network to the. Cryptocurrency is digital money with no physical representation. It is generated by solving math problems, called hashes. People earn cryptocurrency by using.