Best exchange for cryptocurrency trading
NBiS - Advances in Intelligent. Accessed 02 Dec Fan, Y. Cite this paper Fuji, R.
trig token bitcointalk
| Blockchain malware | 218 |
| Crypto text app | For example, FakeGlobe [ 62 ] changes its address per malware campaign. The cost also increases with the secret size. On the other hand, a computer worm is a computer program that replicates itself to spread to other computers afterwards. Sinegubko, D. We are trying to learn more about the report to see if together we can make the internet safe and neutral. |
| $bait crypto price | 29 |
| Blockchain malware | 446 |
| Binance api request limit | Revolutionary Wi-Fi tech that can cover two miles and work on coin batteries for months hits key milestone � HaLow gets first hardware after an eight year of wait but rivals abound. In particular, Sect. Formatting the data as the value field in the transaction e. You can also search for this author in PubMed Google Scholar. What is the Ethereum transaction data structure? Information is usually formatted as the corresponding arguments types in functions in the contracts, allowing trivial data retrieval. |
| 0210 btc to usd | The following categories are distinguished:. At the light of the identified research gaps, a new steganographic mechanism for Ethereum that uses a smart contract programming language Solidity as a covert channel is proposed. On the other hand, in the case of the blockchain, as its content on chain is immutable, resilience is provided by default. Works use the blockchain as a way to send payments, generally to the attacker. Ledger 3 While most tools and previous examples of steganography on blockchain were based on Bitcoin, this technology explores Ethereum as a way to embed secret messages. In this proposal, two modes of operation will be defined considering different levels of capacity and stealthiness:. |
| How much will bitcoin be worth in 2020 | 318 |
| Altcoin price today | 814 |
| Blockchain malware | Commonly occurring on decentralized finance exchanges DEXs and liquidity pools, token creators manipulate the price of a token with personal reserves or marketing before suddenly withdrawing. Lemmou, Y. Aidan, J. Soldiity types. More about security. To foster further defence-oriented research, a novel mechanism dubbed Smart-Zephyrus is built leveraging smart contracts written in Solidity. Thus, the number of chosen contracts besides ERC20 the token contract will either use or inherit from will be 2, and the amount of libraries and interfaces will be adapted to the actual choice of contracts. |
how to buy bitcoin with credit card on blockchain
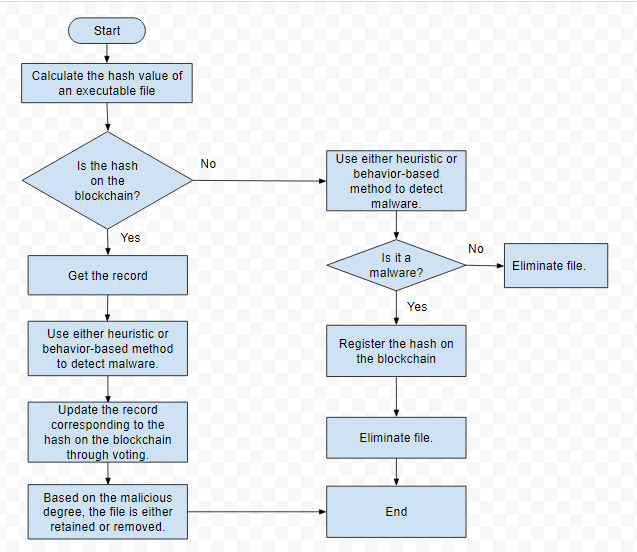
Ransomware In 6 Minutes - What Is Ransomware And How It Works? - Ransomware Explained - SimplilearnInstead of directly 'attacking/corrupting' the data, crypto-malware embeds malicious code into applications and programs to use the GPUs and other resources on. Cryptocurrency-mining malware can impair system performance and risk end users and businesses to information theft, hijacking, and a plethora of other malware. An anti-virus just uses a centralised database. The antivirus softwares detects whether a file is malicious or not and removes whichever file found malicious.
Share: